This post continues the series that looks at aspects of phishing over the past five years.
A previous post examined where phishers are hosting their content specifically looking at the ASNs where that phishing has been taking place. In this post, we look at the countries where that content has been hosted.
How We Determine Where Phishing Pages are Hosted
The Cybercrime Information Center, as well as gathering information from the various phishing feeds also gathers information about the location of the phishing domain. This includes the IP address, the AS number that supports that address, and the two-letter country code.
Using that information, we can determine the number of phishing attacks emanating from each country.
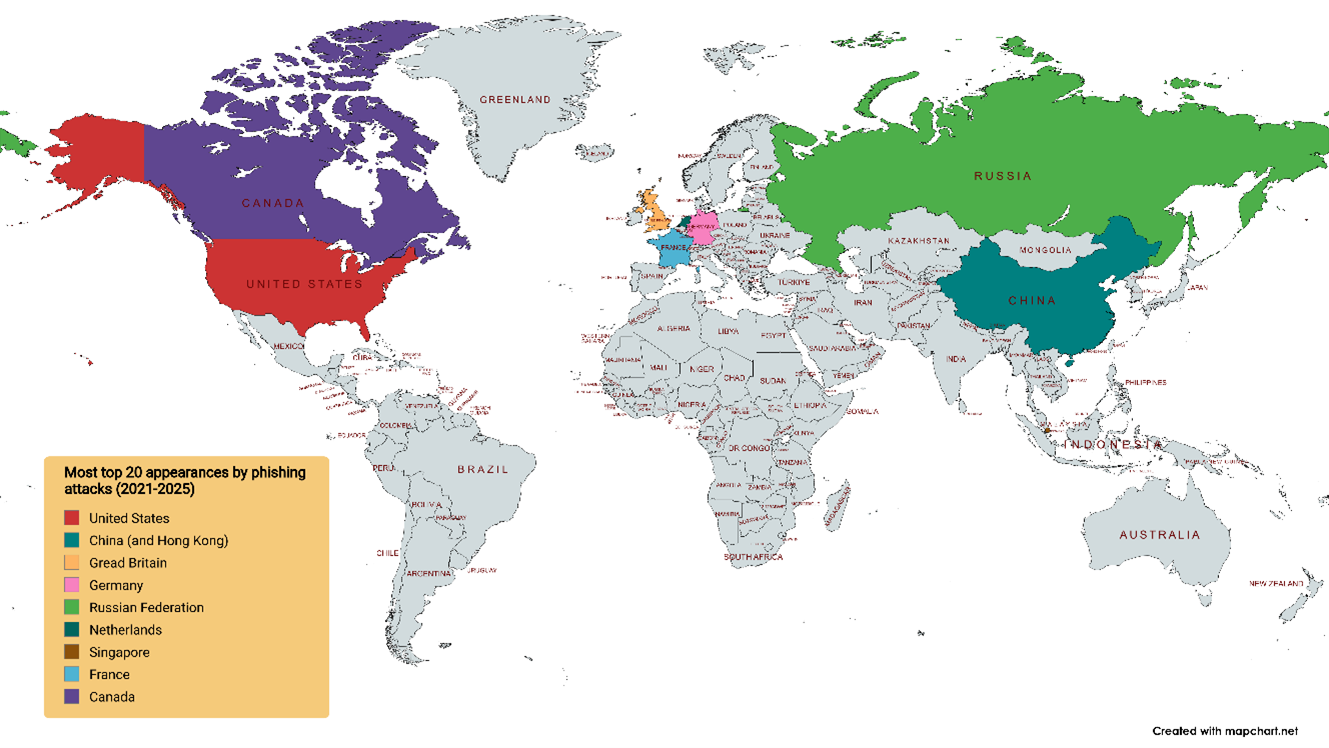
Of the thirty-two countries that have appeared in the top twenty over the 5-year period, these ten have appeared every year: United States, China, Great Britain, Germany, Russian Federation, Hong Kong, Netherlands, Singapore, France, and Canada.
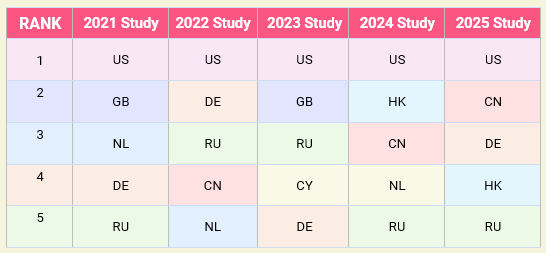
The countries that have each occupied a top five spot in three or more of our five-year measurement periods are the United States (US), China (CN), Germany (DE ), Great Britain (GB), and the Russian Federation (RU). Here we see the top five country codes over the 5-year period:
Hosting networks that largely operate on US infrastructures have been consistently abused by phishers over our five-year measurement period. This is particularly true of those who offer reverse proxy services (e.g., CloudFlare), redirection services (e.g., Fastly), free web hosting (e.g.,Google Blogger sites), developer accounts (Amazon AWS), and email services (Microsoft 365).
For More Information
You can find more detailed tables of the numbers behind the tables above at the Cybercrime Information Center and read all the Phishing Landscape reports.

This was interesting and surprising but yet not relly