Malware activity reports for the quarter are now posted at the Cybercrime Information Center. Our key statistics show small quarter-over-quarter increases in malicious IP address malware records (Traffic Injectors and Attackware) and unique IPv4 addresses reported as serving or distributing malware, and but meaningful decreases in both endpoint and IoT malware reported.
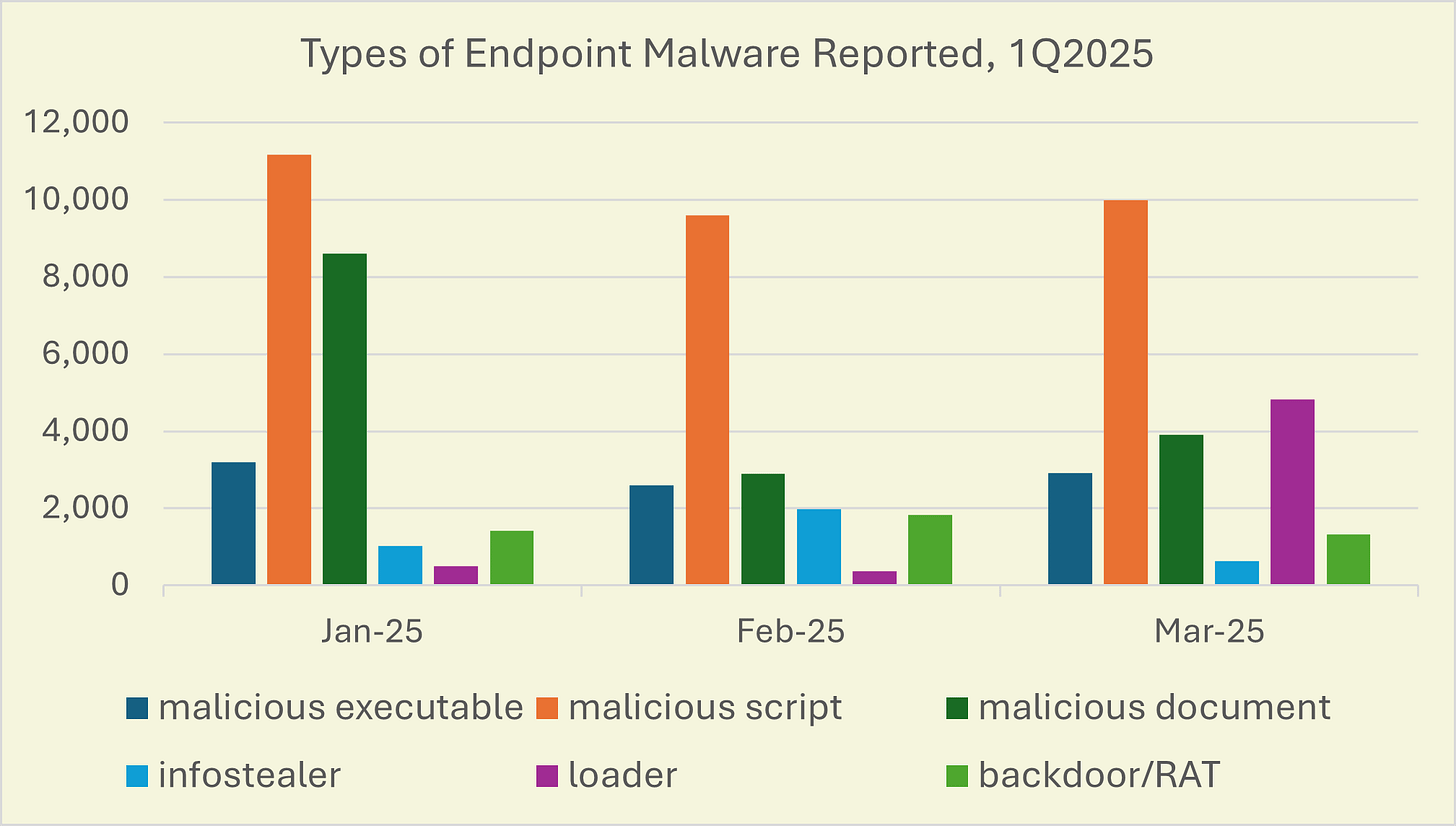
Endpoint Malware
In 1Q2025, the Dow Jones Industrial Average declined 10.5%. In the same quarter, endpoint malware reports – malware that targets user-attended devices – dropped nearly 30% and IoT malware by 40%. So… that’s a win?
Malicious scripts – programs written in Javascript, PHP, shell, or other scripting languages that have been embedded in a web page or a file dropped in a directory – were the most prevalent category of endpoint malware reported. Over 70% of the malicious scripts reported were identified as shell scripts (e.g., command line shell).
Of the ~12,000 malicious documents (files) reported, 90% were identified as WordPress documents. These WordPress malware are often plugins, for example, a fake security tool. Unsurprisingly, wordpress.com was the most victimized domain where WordPress malware was reported: over 1,400 subdomains at wordpress.com and all were found in the /wp-content/uploads directory, a common exploit path for PHP backdoor/RAT malware.
For the quarter period, Gafgyt, Qakbot, and CobaltStrike were the most reported backdoor (RAT), infostealer, and loader, respectively.
IoT Malware
Internet of Things (IoT) malware – malware that targets sensors, wearables, appliances, etc. – declined again this period, down 40%. Another win, and no… not related to tariffs.
The chart below shows the number of IoT devices reported for hosting malware over time.
IoT devices infected with malware surged in 2021 and then declined in August 2023 following a “kill switch event”. Unfortunately, death for malware is not a forever state. IoT malware surged again in November 2024, when the Androxgh0st botnet integrated Mozi payloads.
Malicious Addresses
Nearly 2 million IPv4 addresses were reported for hosting traffic injectors in the quarter. Over 900,000 of these were identified as PHP forum spammers.
690,000 IPv4 addresses were reported for hosting attackware. Of these, nearly 300,000 targeted Secure Shell, SSH.
Hotbeds of hosted malware
During 1Q2025, 1.1 M unique IPv4 addresses were reported as serving or distributing malware. 15,000 ASNs had IPv4 addresses in their assignments reported. Nearly 250,000 unique IPv4 addresses in the AS 9829, Bharat Sanchar Nigam Ltd. were reported, top in the ASN rankings for the quarter. Of the top five ASNs, three are in China: CHINA UNICOM China169 Backbone (AS4837), , China Telecom No.31,Jin-rong Street (AS 4837), and Chunghwa Telecom Co., Ltd (AS 3462). These five account for one half of the IPv4 addresses reported, and are candidates for organizations that adopt a Don't Route Or Peer Lists (DROP) policy.
Summary
Some of the 1Q2025 trends are positive, but malware “busy-ness” is ebb and swell. Malicious scripts should be a major concern for any of your public facing services. If you want to learn how to analyze scripts, check out the resources at ANY.RUN. Malware that injects inappropriate or malicious posts to web forums (comment spam) is also a problem. Consider moderating and particularly reviewing URLs in any comment forms you employ. Lastly, review your threat profile carefully, consider the persistent threat that certain ASNs pose, and decide whether you need to adopt a more aggressive traffic filtering policy at your network perimeter.