Exploiting well known TLD strings in domain names
Colin Strutt
In a recent Interisle Insights post we explained how phishers can choose domain names in such a way as to fool unsuspecting users by making them appear to be valid for the site they think they are reaching.
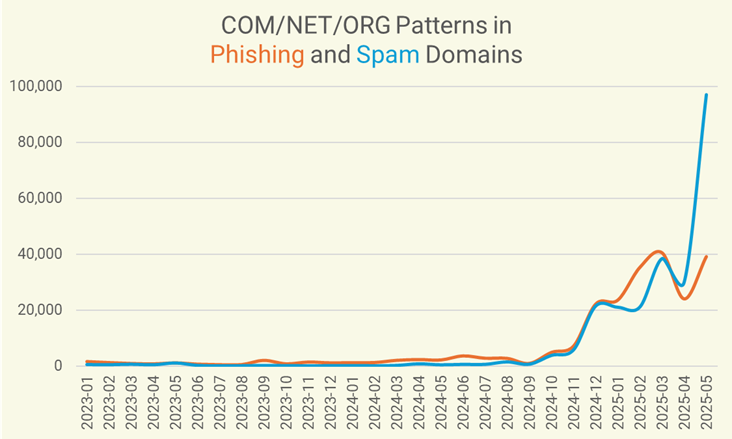
Phishers have adopted another kind of deception in domain name composition: they include well known TLDs within their maliciously registered domain names to confuse users. Specifically, they again exploit a reader’s tendency to see what they want to read rather than what appears in a domain name by including a TLD like .COM, .NET, and .ORG in the domain name.
In such names, phishers typically use a hyphen rather than a dot to attract the reader’s attention to the TLD. Fore example, strings like “-com-”, “-net-”, or “-org-” or names that start with “com-”, “net-”, or “org-” are increasingly common in domain names in our data since November 2024.
This deception is doubly effective on users of small-screen mobile devices, where it is easy for a user to misread a hyphen for a dot and consequently mislead them into visiting a site that they didn’t intend and one that will likely cause them harm.
We’ve observed this naming “convention” in both phishing and spam domain names:
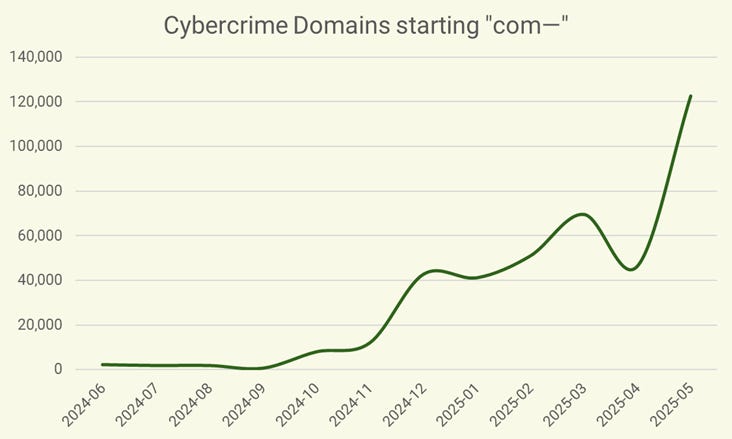
The most frequently occurring names are those that begin with “com-”, e.g.,
com-fastdelivery.shop
com-onlineapplication.shop
com-ticketsua.xin
com-track.online
com-fedexai.vip
com-hold-notice.top
Here we see the rate of growth for only this pattern over the past year:
Round up the usual suspects
Ten TLDs (all new gTLDs) account for 81% of cybercrime domains that begin with the pattern “com-”:
.TOP .VIP .ICU .LIVE .XIN
.XYZ .INFO .CFD .CYOU .WINSix registrars account for 96% of the cybercrime domains that begin with “com-”:
Dominet (HK) – responsible for 55%
Gname
NameSilo
Dynadot
Hefei Juming
Aceville
And five ASNs account for 84% of the hosting for cybercrime domains that start with the pattern “com-”:
Cloudflare AS13335
Tencent AS132203
Amazon AS16509
Hostinger AS47583
Linode AS 63949
Parting Remarks
The lessons that users should take away today are the same as those we indicated in our previous post:
Read the entire URL.
Read what is displayed, not what you expect to be displayed.
Become familiar with the components and syntax of URLs: pay attention to periods and slashes … and hyphens.
Resist the temptation to stop reading once you've encountered a brand or familiar string of characters in URLs.
What Can Be Done … And By Whom?
Some proactive efforts to mitigate phishing and spam seem trivially easy. Registrars and registries could - and should - weed out such obvious cybercrime registrations. For example, registrars and registries can treat such registration attempts as suspicious and delay delegation (pause the registration while staff investigates the legitimacy of the registrant) when they detect attempts to register domain names starting with “com-”, “net-” or “org-” patterns? And why not do so for attempts to register domain names containing “-com-”, “-net-”, or “-org-” as well?