In a recent article, we looked at bulk registration of domain names used for cybercrime based on the data from cybercrime reports in January 2025.
When we reviewed the phishing reports we collected in February 2025 from the Cybercrime Information Center, we found 7,490 sequences of domain registrations that we could classify as bulk registration activity. These accounted for 307,455 cybercrime domains.
Registrars with the bulk of the bulk registrations
Five gTLD registrars through which these bulk domains were registered account for 59% of the total bulk registered domains:
Note that Dynadot, with fewer than 5 million domains under management, had more than 2 ½ times as many domains registered in bulk than GoDaddy, which has nearly 65 million domains in its portfolio. Looking more closely at Dynadot, we found 6 sequences of at least 100 domains, each registered in a matter of seconds, a rate which suggests some form of automation or bulk registration feature:
Overall, we found 50 sequences of at least 100 domains with a registration rate of more than one domain per second.
There was a set of 2,571 domain names registered in bulk through GMO (Onamae.com), all in the .xyz gTLD four months before they were detected for cybercrimes. All were registered between 05:26:20 and 07:09:21 on 10/7/2024 at a rate of 25 domain names per minute in that hundred-minute period. There are two distinct patterns in these domain names; the majority were 8 random characters, and the rest were hyphenated words (one English, the other random characters). Lacking access to contact data for these domain registrations, we cannot confirm that domain names were all registered by the same registrant, but the patterns are clearly suspicious.
Bulk registration sequences can be very long
Several sequences that we identified exceed 1,000 domains. This is an extraordinary number of registrations… and these sequences only count domains that have been tagged as phishing in the time period during which we collected phishing data.
The top 5 gTLD registrars with the longest sequences of bulk registrations account for 42% of the bulk registered domains:
Cybercriminals appear to misuse bulk registration in different ways. Those who are taking advantage of bulk registration tools at GMO or eName are heavy but less frequent hitters, i.e., there are fewer bulk sequences, but the sequences tend to be large. Pricing or the ease by which GMO or eName customers can register enormous numbers of domains are likely factors. Cybercriminals appear to be more frequently hammering bulk domain search tools at Dynadot or GoDaddy, which appear to limit the number of domains per registration session/event.
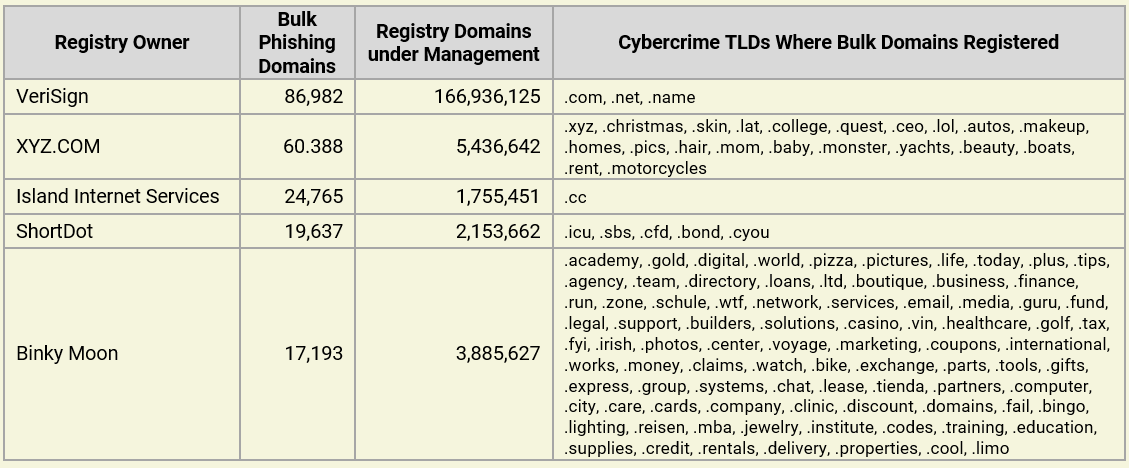
Registry owners
Five gTLD Registry Owners account for 68% of the bulk registered domains:
Note that while XYZ.COM shows fewer overall bulk phishing domains than VeriSign, the total number of domains managed by each registry owner is significantly different. For VeriSign, bulk phishing domains make up only 0.05% of their total managed domains, whereas for XYZ.COM and Island Internet Services, they account for more than 1.1%.
Summary
In our previous article and in our 2024 Cybercrime Supply Chain study, we explain that providing bulk registration services without also providing measures to prevent misuse provides cybercriminals with a tactical advantage over first responders, who must identify, block, and seek to suspend all the domains so registered to fully mitigate a phishing attack. Until policy or regulations are adopted, we will continue to recommend that domain name registrars and registries choose to reduce abuse resulting from bulk registrations.